Goofus and Gallant on Encryption and Government Intrusion
Consider Sen. Tom Cotton and Rep. Justin Amash and guess which is which.


Goofus, despite all historical warnings that this trade-off doesn't work out well for citizens, demands that we all choose security over privacy:
"Apple chose to protect a dead ISIS terrorist's p?rivacy over the security of the American people. The Executive and Legislative Branches have been working with the private sector with the hope of resolving the 'Going Dark' problem. Regrettably, the position Tim Cook and Apple have taken shows that they are unwilling to compromise and that legislation is likely the only way to resolve this issue. The problem of end-to-end encryption isn't just a terrorism issue. It is also a drug-trafficking, kidnapping, and child pornography issue that impacts every state of the Union. It's unfortunate that the great company Apple is becoming the company of choice for terrorists, drug dealers, and sexual predators of all sorts. "
Gallant pays attention and understands that encryption protects citizens from both private fraud and crime, as well as civil rights abuses from governments, both domestic and abroad:
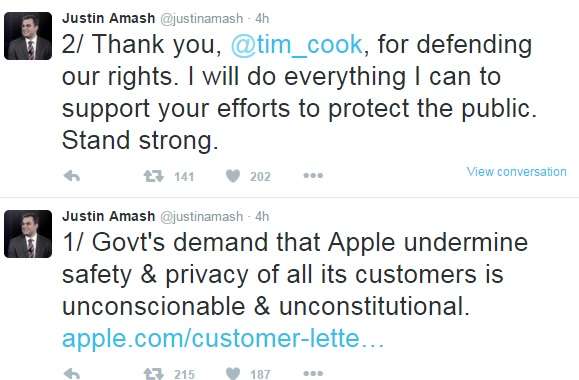
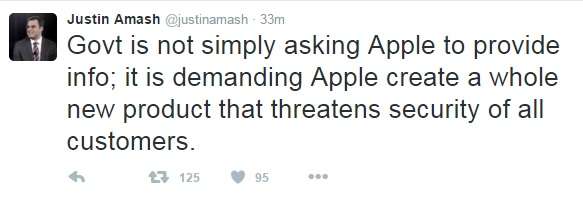
Not up to speed on what's going on? Read here.
Editor's Note: As of February 29, 2024, commenting privileges on reason.com posts are limited to Reason Plus subscribers. Past commenters are grandfathered in for a temporary period. Subscribe here to preserve your ability to comment. Your Reason Plus subscription also gives you an ad-free version of reason.com, along with full access to the digital edition and archives of Reason magazine. We request that comments be civil and on-topic. We do not moderate or assume any responsibility for comments, which are owned by the readers who post them. Comments do not represent the views of reason.com or Reason Foundation. We reserve the right to delete any comment and ban commenters for any reason at any time. Comments may only be edited within 5 minutes of posting. Report abuses.
Please to post comments


Go fuck yourself, Cotton. If I were the CEO of Apple, I'd sue Cotton for libel unless he can prove that convicted terrorists, drug dealers, and sexual predators bought Apple products in a greater proportion than other electronics brand. And a plurality wouldn't cut it, not even a simple majority would cut it. It would have to be an overwhelming majority.
Go fuck yourself, Cotton. If I were the CEO of Apple, I'd sue Cotton for libel unless he can prove that convicted terrorists, drug dealers, and sexual predators bought Apple products in a greater proportion than other electronics brand.
Seriously. Fucking Democrats.
Remember The Wire where the prosecutors got huffy that the pre-paid cellular company was essentially enabling and supporting murderers and drug dealers? I was never sure if the writers were in support of that narrative or against it.
Quit chasing the dragon of author intent, Paul. You never catch it and it's not real anyway.
I thought it was the Rainbow of author intent. At least that exists, but still rather difficult to catch.
Are any intentions real?
No, but they're always good.
God what an asshat. Tom Cotton is overwhelmingly horrible on everything.
It's unfortunate that the gentleman from Arkansas, Tom Cotton, is becoming the Congressman of choice for necrophiliacs, securities fraudsters, and Scientologists of all sorts
Well, he definitely has the psychopath and murdering set , being a national security sweetheart and all.
Sometimes I think Tom Cotton wants my tiara.
But he wouldn't look as faboo in it as you do!
I'm trying to get funding for a National Worst-Off, but most of my prospective backers are balking over the baby-eating round.
I thought Tom Cotton preferred to eat puppies.
Yeah, that may have to be the compromise solution. We'd lose the Planned Parenthood sponsorship but pick up Hormel.
Tell me about it, stud.
Amash continues to shine. Someone tell me why I shouldn't like this guy before I start thinking he's a politician I can believe in.
He's a politician, for starters. Maybe he's an uncommonly good one, but that bar is so low even joe from lowell could step over it easily.
Focus. You'll be fine.
Well I for one wholeheartedly support the terrorists* on this one.
P.S. Fuck off, slaver.
*In this case, "freedom fighters" is the more accurate ten.
Godammit, *term*.
Why legislate? A court already ordered them to do something, after all. Just throw Cook in jail. That should resolve things.
I suppose Cotton fears he might lose, or this will be a one-off.
Why not make everyone in the United States wear a camera that records their life 24 hours a day and stores it on a cloud which can be accessed by law enforcement? All of the arguments they are making for this would apply equally well to my proposal.
Sure my proposal is more far reaching than just letting the government have access to your phone. If it is the case that the government must at all times be able to access your phone without your permission or knowledge, then why should it not be able to do so for any other part of your life?
Cotton would be the first to propose that if he thought he could get away with it.
Exactly - don't give the sonofabitch any ideas, for crissakes!
That is simply the "If it saves just one..." line of reasoning taken to its logical conclusion. The 'safety' nutjobs will gladly lead us into a police state, or if you prefer, an even worse police state.
Someone change Cotton's diaper, I think this one's full.
Poor Mr. Cotton. It must be miserable to be an adult and still be pants-shittingly terrified of the boogeyman.
The man was an Army Ranger. Maybe he's got PTSD up the wazoo.
I've seen some shit man! Shit like you wouldn't believe!
why are only the cunts politically ambitious?
Because wanting to have power over other people's lives is hella cuntish.
The problem of end-to-end encryption isn't just a terrorism issue. It is also a drug-trafficking, kidnapping, and child pornography issue that impacts every state of the Union. It's unfortunate that the great company Apple is becoming the company of choice for terrorists, drug dealers, and sexual predators of all sorts. "
So is locked doors and closed window shades. Should we ban those too?
When I was a teenager and went over to my girlfriend's house, her parents made us leave the door open. Same principle. I mean, if you're not doing anything wrong, you don't have anything to hide, right?
That's why I don't let anyone wear clothes when they come to my home.
Clothes are for closers.
That I understand. What I don't understand is why you make all your guests cover their skin in glitter.
That was just disco night, dude.
Every night is disco night when I'm around.
Man I haven't heard that song in forever.
Sheeyit!
Yeah, that's another great club classic. I love hearing those songs.
So this is our cue to flood the thread with old Soul Train clips, right?
Always a good idea!
Or live
https://www.youtube.com/watch?v=tf0LwyxcQAE
Better than wasting time discussing Tom fucking Cotton.
I feel it is necessary to represent the disco dance moves of my people.
America needs cocaine again.
And Donna Summer
https://www.youtube.com/watch?v=1IdEhvuNxV8
Dammit, HM just lit the Buttplug signal....
Do they have to take them off before they leave or home or just at your porch ;-D
You can leave them on the landing.
You can leave your hat on
So, um, when can I come over?
Vans, cabins in the woods, basements, bedrooms. All should be banned or at least have cameras installed with live feeds to police headquarters.
Paging Evgeny Zamyatin. Evgeny Zamyatin, please pick up a white courtesy phone. No, not the iPhone.
+1 Glass House
"Paris wouldn't have happened" without encrypted apps, says full-of-shit spook.
In an exclusive interview with Yahoo News, Rogers confirmed speculation that began right after the attack: that "some of the communications" of the Paris terrorists "were encrypted," and, as a result, "we did not generate the insights ahead of time. Clearly, had we known, Paris would not have happened."
If we believe they would have known about the plot and stopped it absent encryption sure. But given the number of plots that have succeeded where the terrorists did everything but run an ad in the paper announcing their intentions, what possible reason is there to believe that?
Never mind that we don't know what's on those encrypted messages (that's kind of the point of encryption, after all). Just because they sent encrypted messages doesn't mean those messages contain any details of their planned activities. In order to say "without encryption, there would be no Paris attack" you would have to know the content. The best they can say is "without encryption, we could have seen the content of their messages" which is a useless tautology.
After reading the thread some more, I see that everyone was making the same point.
Clearly, had we known, Paris would not have happened.
This is probably true. If they had known that the Paris attacks were being planned, they probably wouldn't have happened. But that doesn't mean that they wouldn't have happened without encryption.
Wasn't that debunked like a week after the attack? Weren't they mostly using regular old text messaging?
Pretty sure it was less than a week.
Yes it was. And some of them were on multiple watch lists and had known terrorist ties.
Am I the only one whose noticed that this has been kind of a consistent pattern? Most of the actual terrorists have been guys that we were either warned about or should have had pretty good knowledge of terrorist ties just from good, old-fashioned analysis and research. Honestly, that's what I think the advocates of universal surveillance fail to understand - intelligence is the collection and analysis and meaningful distribution of data. The entire "spy-on-everyone" mentality creates a bottleneck in the system by overloading the ability to meaningfully analyze and distribute data with mountains of worthless crap.
Collection is easy. A monkey can build a database and suck up data. Analysis is what is hard. Everyone thinks these guys are out to create 1984. That gives them way too much credit. They are trying to cover their asses. The truth is they have no idea how to do analysis or do their jobs and in their defense their jobs are virtually impossible in some cases. You tell me how we tell which of a hundred Islamic nut cases is going to blow a gasket and start shooting when we know 99 out of the hundred won't ever do shit.
They don't want to or can't admit that truth and are desperate to avoid being blamed when something inevitably happens. So, they constantly try and get more power and collect more information so they can forever say they are doing something and when something happens can blame it on not being able to collect enough. Meanwhile, we lose our privacy and civil rights and are not even made safer in return.
You tell me how we tell which of a hundred Islamic nut cases is going to blow a gasket and start shooting when we know 99 out of the hundred won't ever do shit.
True, but when you get a warning or a reasonable red flag that someone is a nutcase, you just might want to start an investigation or at least focusing your surveillance (and analysis) on that person. Instead, you just get "No, we need to spy on more people!". Think about it. We'd been told by both the Russians and the Saudis that the Tsarnevs were suspicious. The government responded by groping grandma at the airport. Tashfeen Malik was a name change to that of an 11th Century jihadi. The government responded by insisting we need to give hackers a backdoor to our smartphones.
Two things are going on there; they collect so much information that they lose track of the ability to see what is important and they are thanks to the rules of political correctness unable to concentrate on the actual threat. You would think they would be looking up the ass of every Muslim who enters the country. But nope, that would be THE RACIST. So they must treat everyone like they could be a terrorist and pretend the issue has nothing to do with Islam and the real threat is those evil white male "Domestic Extremists".
Also, collecting more useless data makes it that much harder to do good analysis.
The incompetence guarantees that if we give them exactly what they ask for, our safety will be compromised.
Hate to go all Eddie on you, but I felt the need to add something. Yes, analysis is hard. And you make it a shitload harder by throwing a lot of extraneous crap into the the data feed. Scarce resources wind up devoted to trying to sort through Yelp reviews and woodchipper comments on blog comment sections than focusing on the data you'd need to focus on to draw intelligent conclusions.
But even if that was true, it would never justify violating the fundamental liberties of countless innocent people. The spooks expect that people will say their surveillance doesn't increase safety, or that encryption didn't enable the terrorists, but we must also make it clear that trading freedom for safety isn't valid in the first place.
I'd consider the law. On one condition. Any liability for hacking damages will be born by the Junior Senator from Arkansas at the time of the bill's passage.
Notice how no one ever explains what exactly they think might be on this phone that can only be obtained from it. The cell company can tell you exactly who they called and when. If they used a commercial email service, those emails will be stored on the cloud. Its not like the phone records the content of the conversations.
This whole thing is such a fucking sham.
I presume they're looking for possible communications or links to outside groups. Coordination efforts etc.
The cell phone company can give them that info. Every number they called is known.
This presumes they made the connections with standard cell phone calls or communications.
Okay. What will be on that phone that won't be in the cell phone records or on email? If they set up an email account to be accessed on that i-phone, I bet you a hundred dollars the cell phone company can tell you the name of the service. And they likely have the browsing history as well.
So I am still waiting for what they think is on that phone and only that phone.
There are apps that connect to TOR and then to the email service of your choosing. In these cases, the phone company would not know where your email is. Additionally, the phone company can probably tell the government that they connected to (say) Yahoo mail, but probably don't know the account that they used. So the government wouldn't know which account to go get from yahoo. That information would be stored on the phone (likely).
Additionally, many of these other service providers would have their own message encryption. However, depending on the implementation the keys for that subsequent encryption might be stored on the phone and/or encrypted by another password that Apple wouldn't know about.
The point is, getting at the data on their phone very likely could provide additional information that they don't have now. But who cares? It isn't Apple's job to help them.
A savvy terrorist, or indeed anyone who actually gives a fuck about their privacy, would be wiping their phone history clean on a regular basis.
And an unsavy terrorist is likely not going to bother to encrypt in the first place.
And also not likely to even be noticed by the security bureaucracy.
If the email service encrypted it, they would have to by law have to have stored it and have the ability to unencrypt it when given a court order to do so.
This is not about that phone containing any special information. This is about the FBI being too lazy to investigate and wanting to just look at the phone.
What is there to investigate? The perpetrators killed themselves, and whatever assistants they thought they had chickened out. At best we'll spend millions tracking down, prosecuting, and jailing people too chicken-shit to actually cause any harm.
Of course, once I put my government hat on, I realize it's mostly just about making up reasons to spend millions.
There might be other "terrorists" whose only connection to the killers is contained in that cell phone. The entire thing is pathetic. If it wasn't so serious, it would be funny.
This is not true.
1) Again, when you go to a mail provider, typical logging just says you went to a site (like gmail.com). The phone company would have to a) inspect the connection and b) decrypt the encryption between the device and the mail provider in order to know what your credentials were.
2) Since the phone company doesn't know which account you used, the government cannot easily go to Google or Yahoo to say "Give me the emails in this mailbox". That information is typically on the phone.
3) There are services that allow you to send messages that are encrypted on the phone. Even if they are stored on the cloud, the cloud owner does not have the keys to decrypt the messages. They are just storing a bunch of data that they cannot read.
There is very likely information on the phone that the government could not access otherwise. And that's the point. Who would care about Apple encrypting our phones if the government could get that data otherwise?
There is very likely information on the phone that the government could not access otherwise.
The chances of that information being valuable to the investigation or providing leads to other terrorist cells is very small. To believe there is such information, you have to believe these people were so careful that they left no other trail and I find that highly unlikely.
I just gave you an example that could happen regularly.
An attack from a terrorist who was not detected and therefore who was not being monitored. After the fact, you want to know their contacts. If they were only using email (not phone calls) then you need to know what email account (or irc handle, or tor chat identity, etc) they were using.
If you know their ISP and their Phone Company you don't know their email account. You MAY only know the email provider. In these cases, the phone and/or their computer may be the only place that has data about the identity they used to contact these places.
Again, what is the point of Apple encrypting this information if it could be discovered by the government anyways? The whole reason encryption is valuable to criminals is THE SAME REASON it is valuable to law abiding citizens. Apple is telling everyone that encryption protects this vital data. Is Apple lying?
Explicit picture of teenagers, or myterrormap.doc, maybe hereswhereihidthenuke.jpg.
Most likely Hillary's work emails as it was a government phone that was purchased and issued by the county.
Then I blame the country. What the fuck is the country doing letting their employees encrypt government issued phones without the county knowing about it and having the key?
Government data NEEDS to be encrypted, lest it fall into the wrong hands. Duh!
Okay. What will be on that phone that won't be in the cell phone records or on email?
I think that's what the FBI intends to find out. I have a ton of data on my phone about my personal life that has never once traveled through a text message, email or cellular call.
The NSA has the contents of the phone conversation. Just ask them for it.
Yeah, it's not about his phone. It never was.
^This.
Yes Tonio, that is what I said. Thanks for agreeing.
What's most terrifying is I honestly don't believe that Cotton and his ilk consider what they are proposing to be "big government." Even if you devolve into a utilitarian analysis the chances and threat to our freedoms of a terrorist attack are infinitely smaller than the threat of a government that possesses the ability to conduct mass domestic surveillance on nearly all of its citizens.
And if the government possesses it, then so will everyone else. What's that do to the economy when you can't trust the safety of your electronic data?
This police security state bullshit is infuriating to me. We've had plenty of warnings about Big Brother over the decades and yet people still don't get it. In this case, the people who are supposed to be the "protectors" are purposely attempting to make us all less safe so that they can have more power. It's not really surprising. What is surprising is how many bootlickers out there are suckered into supporting this under the fake terrorism scaremongering (see Jazz Shaw's state fellating article about this at Hot Air). Whatever they get off that phone is no where near worth putting all of our personal data at greater risk. The security state and all it's sycophants are all traitors. If you can't do your job without any restrictions on your power then you should find a different job.
Jazz Shaw has shit his pants so mightily that, lo, he cannot shit any more unto his britches, and the shit hath backed up his tract and overfloweth out his fingertips, through his keyboard, and onto the greater Internet.
If he wasn't always wearing that stupid hat, it'd burst from his ears and his fontanel, too.
Fucking externalities.
What do Amos and Andy have to say?
I don't understand. Hasn't Apple said that they CAN'T defeat their own encryption? Why doesn't Cook just tell that to the judge and be done with it? Why is he making it seem like they can?
The iOS situation does allow for what is called a "malicious update," i.e., an OS update that would have defeasible security.
So Apple was lying? From Cook's letter "We have even put that data out of our own reach, because we believe the contents of your iPhone are none of our business." But it's really "We could get your data if we wanted to"?
The data is out of their own reach unless they write a whole new OS.
Right. So it's not out of their reach.
Which also means it's not out of ANYONE'S reach. So there's no need to enslave Apple to do anything.
The judge is ordering them to develop it for the feds. Basically like slavery only more evil.
Apple is being "asked" to create a backdoor for gov use.
They're being asked to disable the mechanism that wipes the hard drive after 10 unsuccessful login attempts, not to decrypt the hard drive. The FBI wants to brute force it.
If they can brute force the password the hard drive will decrypt itself so it's that same thing.
I don't understand. Hasn't Apple said that they CAN'T defeat their own encryption?
Read the previous thread on this subject, it's informative. Apple CAN'T (read: shouldn't) be able to defeat their own encryption. The government is trying to get apple to allow them to circumvent the 2nd order protections (password failure leading to auto-delete).
Which would defeat Apple's encryption. It's a roundabout solution but it is a solution, know what mean. So again, Apple is lying if they can do that.
I don't disagree.
What's interesting to me from the engineering standpoint, is once again, it's the endpoints, stupid. The encryption Apple has is fine, but the weak link is the fact that everyone "knows" it's protected nominally by a 4 digit code. So- putting the legal issues aside, if we go back to agreeing that protecting your data is your responsibility-- we're protecting our data from a snoopy government with excellent 256 bit encryption and a 4 number pin. And further, it relies entirely on Apple's veracity as an institution to successfully fight off a judicial order.
We should always be striving for protection in which those niceties of law and judges whims don't matter.
At least the Muslim terrorists kill themselves. Tom Cotton is even more dangerous.
KDW does not disappoint:
http://www.nationalreview.com/.....nts-demand
He's really writing for the wrong publication.
No way. He's antiabortion and therefore icky. Can't have that type of yokeltarian nonsense polluting my pure libertarianism. Let him stay with Kathryn Jean Lopez and the other cervix inspectors at NRO.
I keep having this thought, too. You guys have explained the situation pretty well, so I feel I have a decent grasp on it, but the fact that they are forcing Apple to help them instead of doing it on their own is not surprising, but it is pretty pathetic.
Its not that they can't. They could if they wanted to. It is that they are lazy and want apple to do their work for them.
That is even worse.
Next up the government will pass a law mandating that padlocks be made only from balsa wood.
All subjects must register their passwords with the Ministry of Privacy.
And NO SLANG!
More likely it will be a felony for not leaving the key under the doormat or in the mailbox.
Isn't Amash an Arab? No wonder he's siding with the terrorists.
/sarcasm
I'm up to speed. Apple should IMMEDIATELY turn over the info asked for. The terrorist is dead. He therefore has no rights. And it does not follow that anyone else's rights would be violated now or in the future by such an action.
Goofus and Doofus, I like it.
http://www.Anon-Net.tk
The technology is so developed that we can watch videos, live streaming, TV serials and any of our missed programs within our mobiles and PCs. Showbox
All we need is a mobile or PC with a very good internet connection. There are many applications by which we can enjoy videos, our missed programs, live streaming etc.