OMG! U.S. Central Command Hacked by Terrorists! Er … Not Exactly
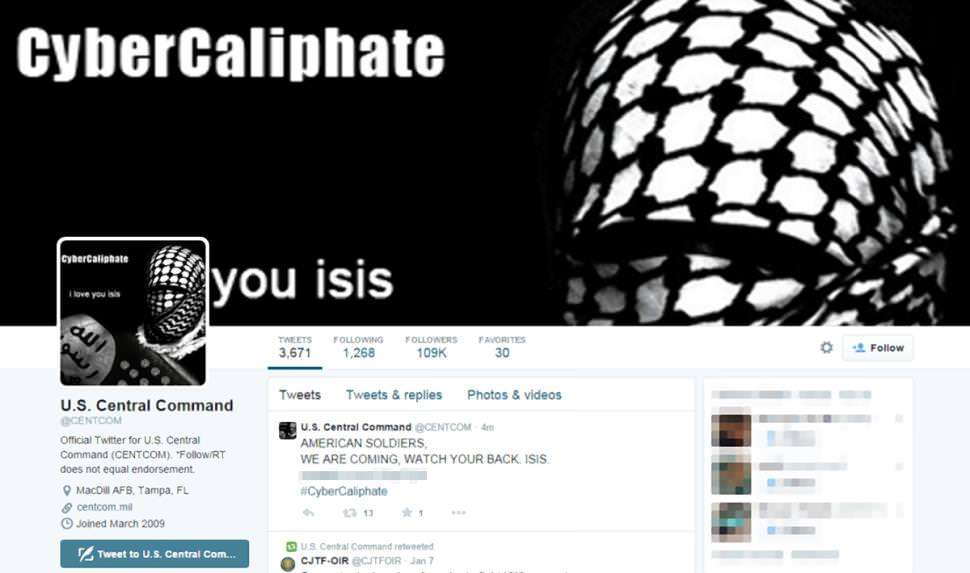
So while President Barack Obama was presenting his plan to regulate students' online privacy to reduce the ability of businesses to target them with advertising, somebody seized the Twitter feed and YouTube account for the U.S. Central Command. For a short time, it appeared as though the Islamic State had taken control of the feed and was posting all sorts of secret U.S. intelligence, like maps and personnel information.
Until people started looking closely. It turned out none of it was actually classified information. The slides and maps could be easily sourced online. The personnel information was not particularly secretive information. Some of it looked like it was from military post or base directories that are easily available. From the Associated Press:
Most of the material was labeled "FOUO," which means "For Official Use Only," but none of it appeared to be classified or sensitive information, suggesting the hackers did not breach classified material.
One of the documents appeared to be slides developed by the Massachusetts Institute of Technology's Lincoln Laboratory, a federally funded research and development center focused on national security. The slides appeared to depict what it called "scenarios" for conflict with North Korea and China.
"This is little more than a prank or vandalism. It's inconvenient and it's an annoyance. But that's all it is," said Col. Steve Warren, a Pentagon spokesman. "It in no way compromises our operations in any way shape or form."
What appears to be the same hacker or hackers took over the Twitter feed of a Maryland CBS affiliate last week. Whether these folks have actual strong beliefs in support of Islamic terrorism or if they are just pranksters is an open question.
In any event, there's no sign that Central Command itself was hacked. Somebody got access to their social media accounts. That's obviously not the same thing as getting access to the classified data storage.
Editor's Note: As of February 29, 2024, commenting privileges on reason.com posts are limited to Reason Plus subscribers. Past commenters are grandfathered in for a temporary period. Subscribe here to preserve your ability to comment. Your Reason Plus subscription also gives you an ad-free version of reason.com, along with full access to the digital edition and archives of Reason magazine. We request that comments be civil and on-topic. We do not moderate or assume any responsibility for comments, which are owned by the readers who post them. Comments do not represent the views of reason.com or Reason Foundation. We reserve the right to delete any comment and ban commenters for any reason at any time. Comments may only be edited within 5 minutes of posting. Report abuses.
Please to post comments


They should have had someone in charge who's really competent with information security, like the people in charge of hiding Obama's college records.
Valerie Jarrett?
Somebody got access to their social media accounts. That's obviously not the same thing as getting access to the classified data storage.
There are those who might claim that, in these days of modern times, it's *worse*.
If super-secret material was compromised, would they readily admit it?
Sad when you can't believe a single word your government tells you, isn't it? Not that you should even when it is more trustworthy than the current iteration, but still.
"Not only was super-secret material compromised, it was done by the North Korean government!"
What a useful scapegoat North Korea has become.
Thank God they didn't seriously threaten US security by posting pics under the US Central Command page of Barack Obama with a wang photoshopped on his head.
The only rational response would be for his followers to start shooting up internet cafes all over the Middle East.
His followers DON'T HAVE ANY GUNS, mad, cause ICKY!
They'd pummel the mideast with hashtags, though. BURY the fuckers in hashtags.
They wouldn't have hacked anything classified as confidential or higher since those computers are kept on networks wholly separate from the non-secure network that is hooked up to the internet. Occasionally there's some idiot who plugs in a laptop with a classified drive to the non-secure network, but that's usually caught quickly before there's any classified file spillage.
Occasionally there's some idiot who plugs in a laptop with a classified drive to the non-secure network, but that's usually caught quickly before there's any classified file spillage.
Except, of course, when Microsoft systems are involved.
As far as I know, DoD doesn't use Windows 8.1.
I'd have thought that before some lower-level contractor walked off with all the NSA data he could eat.
That's only because Snowden had physical access to the secured network. He wouldn't have been able to hack it from home.
Turns out "obamasucks" was not a very secure password.
+1 high- low-strength password
I got concerned when they posted, "All ur base are belong to us."
I bet this was all Snowden's doing!
Lets roll with it man. Wow.
http://www.Web-Privacy.tk