OMG! U.S. Central Command Hacked by Terrorists! Er … Not Exactly
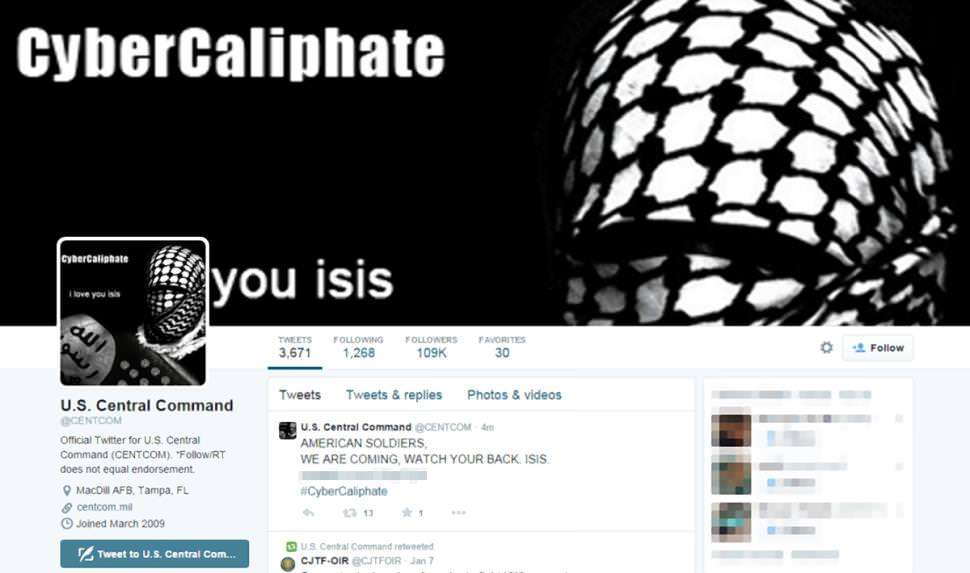
So while President Barack Obama was presenting his plan to regulate students' online privacy to reduce the ability of businesses to target them with advertising, somebody seized the Twitter feed and YouTube account for the U.S. Central Command. For a short time, it appeared as though the Islamic State had taken control of the feed and was posting all sorts of secret U.S. intelligence, like maps and personnel information.
Until people started looking closely. It turned out none of it was actually classified information. The slides and maps could be easily sourced online. The personnel information was not particularly secretive information. Some of it looked like it was from military post or base directories that are easily available. From the Associated Press:
Most of the material was labeled "FOUO," which means "For Official Use Only," but none of it appeared to be classified or sensitive information, suggesting the hackers did not breach classified material.
One of the documents appeared to be slides developed by the Massachusetts Institute of Technology's Lincoln Laboratory, a federally funded research and development center focused on national security. The slides appeared to depict what it called "scenarios" for conflict with North Korea and China.
"This is little more than a prank or vandalism. It's inconvenient and it's an annoyance. But that's all it is," said Col. Steve Warren, a Pentagon spokesman. "It in no way compromises our operations in any way shape or form."
What appears to be the same hacker or hackers took over the Twitter feed of a Maryland CBS affiliate last week. Whether these folks have actual strong beliefs in support of Islamic terrorism or if they are just pranksters is an open question.
In any event, there's no sign that Central Command itself was hacked. Somebody got access to their social media accounts. That's obviously not the same thing as getting access to the classified data storage.
