'Complete Control': Notorious Surveillance Contractor Tech Uncovered


Hacking Team, a company which has been described as an "enemy of the Internet," provides law enforcement and intelligence agencies with legal "offensive technology" to infiltrate and remotely control people's phones and other digital devices. The extent of this company's capabilities remain murky, but two groups of Internet security experts say they have just exposed some of their surveillance firepower and the fact that Hacking Team has more servers spitting out malware based in the U.S. than any other country.
"Our latest research has identified mobile modules that work on all well-known mobile platforms, including as Android and iOS" as well as Windows Mobile and BlackBerry, announced the Russian-based Kaspersky Lab on Tuesday. "These modules … translate into complete control over the environment in and near a victim's computer." Indeed, the governments who use Hacking Team technology can turn on a cellphone's microphone, camera, and GPS unnoticed. They can also access people's email, call history, chats, browsing history, among many other potentially incriminating data.
"It's long been known that law enforcement and intelligence agencies worldwide use Hacking Team's tools to spy on computer and mobile phone users—including, in some countries, to spy on political dissidents, journalists and human rights advocates," explains Wired. "This is the first time, however, that the modules used to spy on mobile phone users have been uncovered in the wild and reverse-engineered."
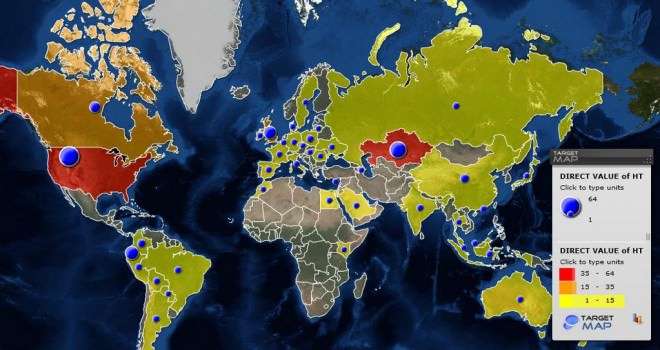
One of the biggest doozies of the Kaspersky Lab report is that the U.S., by far, houses the most Hacking Team servers, which are part of a "huge infrastructure that is used to control the [remote control system] malware implants." There are 64 known servers here, compared to 49 in Kazakhstan, 35 in Ecuador, 32 in the United Kingdom. Most of the other 40 countries that the lab traced Hacking Team malware back to have only one or two servers.
The lab cautions, "we can't be sure that the servers in a certain country are used by that specific country's LEAs [law enforcement agencies]; however, it would make sense for LEAs to put their [command and control servers] in their own countries in order to avoid cross-border legal problems and the seizure of servers." Likewise, it's no secret that the company has aggressively marketed itself to American government officials.
Hacking Team spokesman Eric Rabe quick to downplay the findings as "old news," according to the Associated Press. "We believe the software we provide is essential for law enforcement and for the safety of all in an age when terrorists, drug dealers and sex traffickers and other criminals routinely use the Internet and mobile communications to carry out their crimes," he assured.
However, Citizen Lab at the University of Toronto, which produced a report alongside Kaspersky Lab's and has long kept an eye on Hacking Team, reitereates that the company's products have a history of being used to target journalists and activists around the world.
"This in many ways is the police surveillance of the now and the future," cautions Morgan Marquis-Boire, a lead author on the report and a security researcher with Citizen Lab. "What we need to actually decide how we're comfortable with it being used and under what circumstances."
Editor's Note: As of February 29, 2024, commenting privileges on reason.com posts are limited to Reason Plus subscribers. Past commenters are grandfathered in for a temporary period. Subscribe here to preserve your ability to comment. Your Reason Plus subscription also gives you an ad-free version of reason.com, along with full access to the digital edition and archives of Reason magazine. We request that comments be civil and on-topic. We do not moderate or assume any responsibility for comments, which are owned by the readers who post them. Comments do not represent the views of reason.com or Reason Foundation. We reserve the right to delete any comment and ban commenters for any reason at any time. Comments may only be edited within 5 minutes of posting. Report abuses.
Please to post comments


http://www.dailymail.co.uk/tvs.....cDaid.html
She sure don't look 50. Dang.
"terrorists, drug dealers and sex traffickers"
A trifecta of non-existent threats, or threats caused by government interference in the first place.
My thought, exactly.
Terrorists are a threat and they were not created by 'government interference', unless you count the Iranian and Saudi efforts to fund them.
They are not a threat in the sense that the chances of me being killed by one are extremely remote, as opposed to a car accident, heart disease, or cancer.
Or lightening on a sunny day.
Terrorists are a threat
Regardless of origin, terrorists are a threat the same way, bees, sharks, and lightening are a threat.
Tylenol, which kills several hundred Americans every year for decades, is a far greater threat to our way of life than terrorists.
I wouldn't say sex traffickers are technically due to government intervention. There are plenty of sex traffickers that target children. Child prostitution should remain illegal. But consenting adults should be able to do exchange money for sex.
"There are plenty of sex traffickers that target children."
Are there really? How many are "plenty"?
How about, instead of arguing about plenty, could you agree to an industry-wide bias towards youth and a general disregard for the law?
Worldwide, almost 20% of all trafficking victims are children. However, in some parts of Africa and the Mekong region, children are the majority (up to 100% in parts of West Africa).
And not all human trafficking is for sex. There is a lot for forced labor, which again should always remain illegal.
I hope you'll forgive me if I take a United Nations Office on Drugs and Crime Report with a huge grain of salt.
And this is legal how?
Since when did law enforcement have to follow the law?
Under yesterday's ruling, it seems the cops need a warrant.
But you're not under arrest, we're just searching.
Because fuck you, that's why.
+1
The phone designers are not able to prevent the remote control? Or not allowed?
Says iOS has to be jailbroken first.
Of course. But the age old tug-of-war between flexibility/power runs into stodgy safety.
There was a time (in the old days) when you couldn't get a virus when reading an email. It was physically impossible.
Then came along Microsoft and the desire to integrate "Active Content" within emails and BLAM, now you can be compromised by merely opening the email, attachments be damned.
As long as phone providers and os mfgs provide an API to turn on cameras, turn on speakers, allow sophisticated controls, you open the door to unauthorized use. The more complex the features, the more likely the loopholes, the more difficult to plug them.
Yo, fuck these guys.
If this is external malware, can't it be blocked by your firewall, etc.?
Now that Kaspersky has identified it, I assume their software will block it? Interesting that I don't see them saying that, although I scanned the linked article and may have missed it.
Yes. Any 'legitimate' law enforcement tool which acts like malware or displays malware heuristics can be blocked by any firewall/antivirus/security measure.
A root kit is a root kit is a root kit, it doesn't matter whether it was written by a GS-12 or a teenager in Malaysia.
What could happen, is that our fine government "gets to" malware/spyware/firewall/security firms and demands a 'back door' to allow any malware with 'X' signature to pass through.
This is harder than demanding back doors to encryption, because fewer encryption standards exist. But never underestimate the government's ability to ban or regulate something through sheer force of will.
But never underestimate the government's ability to ban or regulate something through sheer force of will.
You love saying this, but black markets are real.
And so are the life sentences the people who ran them are serving.
The government still can't stop it. Never underestimate the ability of technology and ingenuity to undermine government bans and regulation.
So you're saying the life sentences are not a deterrent.
64 servers in the US? Sounds like our govt's a significant piece of their revenue stream.
My concern here is that we're whining about Tazer International, and not whining about the officials that use these tools.
It's like we're saying the right people are in charge, but the wrong tools are being used, no?
No, we're saying the tools wouldn't exist if the power wasn't granted to anyone in the first place.
Sure, the tools would probably exist in a more rudimentary form, but by the sheer coercion of taxpayers the officials can funnel these malinvested dollars to a company that would otherwise have little to no revenue.
well its encouraging to see that we are equally as concerned with Rule of Law and the rights of our citizenry as Kazakhstan.
Any area nerds got tips for protection against this kind of thing?
Not for you.
You're more pathetic everyday it seems.
Given what I'm reading here, good firewall and anti-virus/malware (preferably real time) protection should do the trick.
I'm not as versed with anti-virus/malware on the cell phone platform so I can't speak to that.
Samsung, however, since the KitKat update is nagging me daily about some kind of 'security update' it wants to do on my phone automatically.
I wince at anything the manufacturer wants to download and run automatically so I keep declining.
I haven't decided if that's a prudent move or not.
Have you ever had an update to a piece of working software that made your life better? I haven't. The update in the best case is benign, but more likely, it will bloat my system and cause performance drops. The worse was when AT&T decided to push an OS update to my Samsung S3, and since then my battery life went to crap and the phone would get hot for no particular reason. And for what? I've decide to deny all automatics update since.
http://www.dailymail.co.uk/new.....prank.html
Should have thrown a flashbang instead. Then nothing else would have happened.
Morelli is a retard, and should be promoted to police captain post haste.
At minimum, Morelli would have ruined the fuck out of whatever object that sparkler landed on.
'He just goes off and does what he wants to do at that time,' Brian Goralnik, a neighbor who grew up with Morelli, told WFSB.
'At some point, you would think that maybe he'd find the right light, the right way, and he just couldn't find that.'
Another neighbor, Linda Selander, told WTNH that she was 'semi shocked' to learn that Morelli was allegedly involved. She explained that the teenager crashed his mother's truck in her yard last year.
'All I wanted was for him to come over and apologize and say "hey I didn't mean to do it" and he didn't,' she said.
Does whatever he wants and doesn't apologize for destroying other peoples' property? He definitely missed his calling.
Similar happened at UVA in the late 90s. DA declined to prosecute the two guys who threw two smoke bombs into the girl's apartment because her parents said they didn't want more lives ruined by this stupid tragedy.
"What we need to actually decide how we're comfortable with it being used and under what circumstances."
I really hope someone prepares Haking Team for the realistic feedback that the average American is not ever going to be comfortable with the prospect of being an advanced target of this kind of surveillance.
Hacking Team spokesman Eric Rabe
... is setting himself up to be royally hacked unless Eric Rabe isn't his real name.
Who's the Bataan death march survivor with her?
Courtney Cox.
Is this more to your liking?
I like how the only choice is Courtney Cox or the actress from Identity Thief.
Nothing inbetween. Nothing at all.
There's plenty thinner than CC. I thought she was in between.