The Volokh Conspiracy
Mostly law professors | Sometimes contrarian | Often libertarian | Always independent
Google Chrome Now Blocks Insecure Downloads from Secure Websites. Many Court Website are Insecure.
Chrome now blocks download links on How Appealing from insecure court sites.
Much like people, web sites can be insecure. Unlike people, you can easily determine whether a web site is insecure. In the address bar of your browser, you should see a lock icon next to "reason.com/volokh/". Click that lock. A box will popup showing that the connection is secure. All responsible web sites have security certificates. These simple licenses tell users that information can be securely uploaded and downloaded.
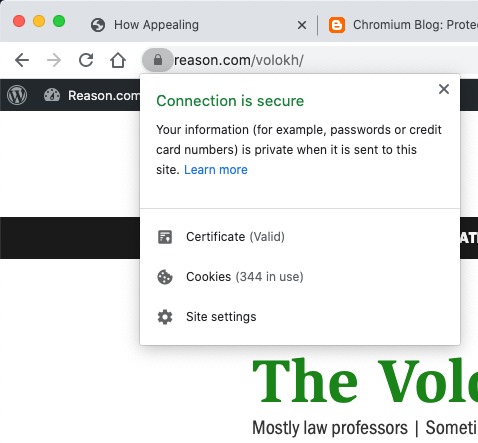
SupremeCourt.gov, a responsible web site, is secure.
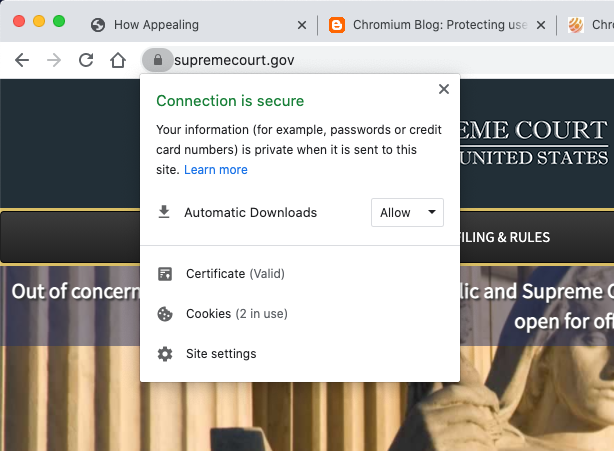
And most of federal courts of appeals are secure. The First, Second, Third, Fourth, Sixth, Eighth, Ninth, Tenth, Eleventh, and D.C. Circuits are secure.
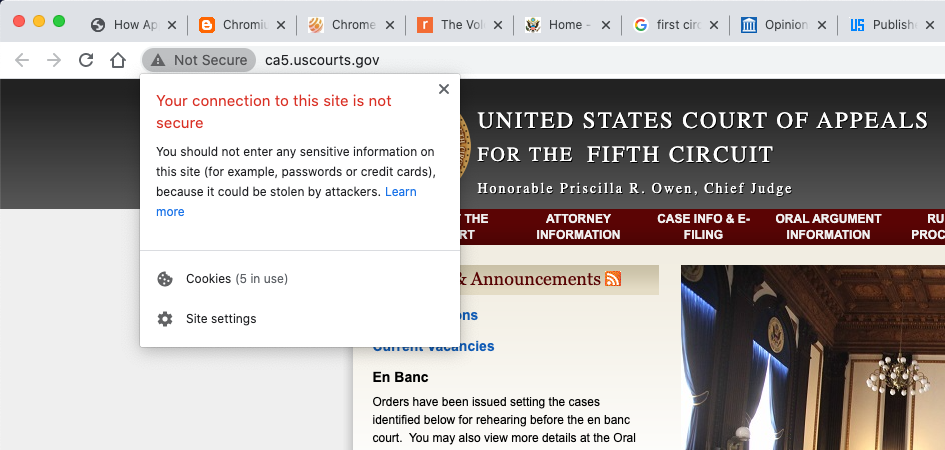
Other courts of appeal are not secure. The Fifth Circuit is insecure.
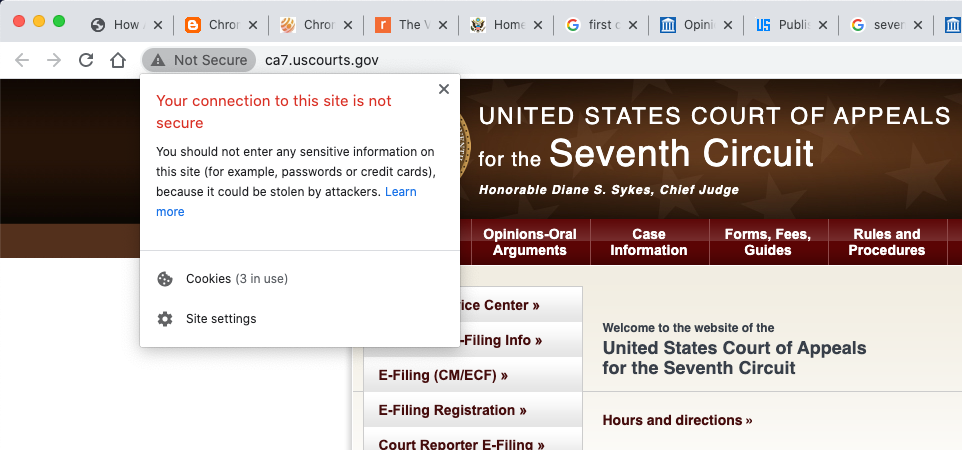
The Seventh Circuit is also insecure.
And the Federal Circuit--the so-called tech court!--is not secure. No wonder the Supreme Court reverses them all the time!
Some state courts are also insecure. For example, the Pennsylvania Supreme Court. Perhaps the independent state legislature can remedy this problem. (Kidding, kidding).
Regrettably, my home state is no better. Hackers can mess with Texas. We defended the Alamo. Certainly we can defend a web site.
Going forward, these insecure courts, and many others, should become secure. Why? The latest version of the Google Chrome browser is blocking downloads on a secure page to an insecure site. If I include a link to a PDF from any of these insecure sites, it would be blocked. Far worse, How Appealing (a secure site) can no longer link to PDFs on any of these insecure sites. Howard Bashman is a national treasure. I know judges routinely check his site. Now, Howard's links will not work.
I stumbled across this problem today by accident. I tried to download a recent Fifth Circuit opinion, but I couldn't. But when I visited the Fifth Circuit's site, I was able to download the opinion from the Opinions page. With all due respect, Court web sites should be secure. These certificates are not difficult to install. And the failure to fortify these sites will make it tougher for people to access the law.
I will report back in due course to see if these sites become secure. For now, there is an easy workaround: (1) Right click on the link, (2) click "Copy Link Address," (3) paste that link into your address bar. The file will download since the request is not coming from a secured page.
Editor's Note: We invite comments and request that they be civil and on-topic. We do not moderate or assume any responsibility for comments, which are owned by the readers who post them. Comments do not represent the views of Reason.com or Reason Foundation. We reserve the right to delete any comment for any reason at any time. Comments may only be edited within 5 minutes of posting. Report abuses.
Please to post comments


Hacking should be a capital crime, with trial in absentia, and summary executions by drone, around the world, with legal immunity for all collateral damage, including families. To deter.
Why, exactly, should being good at computers be a capital crime?
Is the origin of this opinion a deep-seated insecurity on your part that you, yourself, are NOT good at computers?
There's a difference between being good with locks, and going around breaking into people's homes by picking their locks.
Indeed there is. Would you demand that locksmithing be a capital crime, punishable by extrajudicial killing? As the jackass above does for being good at understanding how computers work?
I think his point is that there is a difference between having a skill and misusing it to commit crime. Your comments conflate the two.
In the Old West, stealing a horse was a capital crime. Because people were completely dependent on horses, and stealing someone's horse would devastate him, perhaps endanger his life. One could argue the same think applies today to computers.
For the record, I don't advocate that. Ten years under the CFAA should be enough for most hackers.
"I think his point is that there is a difference between having a skill and misusing it to commit crime. Your comments conflate the two."
I think he used a word but does not know what it means, and this is also true of you, which is why you accuse me of conflating two things when you're the one who has done this.
You seem to be deliberately obtuse on this point. Is that the case? In the case of any skill, the the application to commit a crime would be punishable under appropriate laws, yes? Behar is a bit over the top with his recommended punishment, yes, but your thin-skinned reaction is little better.
"You seem to be deliberately obtuse on this point. Is that the case?"
No more than you, and at least I get the terminology correct.
" In the case of any skill, the the application to commit a crime would be punishable under appropriate laws, yes?"
He's advocated punishing anyone who has the skill, which is not a crime.
No, but I do think we should view it as piracy and hold the nations that nonchalantly permit it responsible for it.
that would be us more than any other nation.
Should Congress issue letters of marque and reprisal to US hackers?
Honestly, probably not the worst idea.
I would suggest not using Google Chrome if you value your privacy and/or if you want the internet to remain free to all viewpoints and free to access using non-Google browsers.
I disagree with that on everything but the privacy. Yes chrome isn't going to bend over backwards to let you block ads and isn't as privacy friendly as Firefox but for the most part Google has the opposite incentives.
Google's great fear is companies creating their own walked gardens (think apple or Samsung giving affiliated sites better perf on their hardware ). Google specifically started chrome exactly to limit Microsoft's ability to do that and as they have a competitive advantage on the open internet it's very much in their interest to work with other organizations to keep the internet using open protocols.
As far as privacy goes they have mixed incentives. In general they want to block the less scrupulous ad networks that do what they can to fingerprint your browser and track you even over sensitive sites but you are correct they are going to make the easiest to use default to allow Google to gather data for ads etc.. Personally I like that and have no objection but to each their own
Some people trust Google, and some do not, in ways that are resistive to actual evidence about Google's trustworthiness in general or in specific cases.
In general, I think Google sees it's best approach is to deliver people what they want, to keep them from wandering off to other providers, but I tend to prefer open-source software. (a high-tech version of Reagan's "trust, but verify", perhaps.)
The whole article is about how chrome decides not to load stuff Google doesn’t like. That’s not free and open.
Your choice to use tools supplied by Google was yours. I can't say how free or open this choice was, but it isn't Google that 's limited the freedom or openness of it.
"Insecure" in this context mean that any download or upload to the website is not encrypted but sent in clear text. It does not mean that it is easy to hack it. Ease or difficulty in hacking depends on how tight the rules are on the firewall behind which the web server is situated.
Well sorta. I mean absent a cert you are potentially vulnerable to DNS hijacking (depending on your resolver conf, websites use of DNSSEC and whether someone is launching a MITM attack between you and resolver).
But yes, generally speaking this isn't likely to be dangerous so unless you are likely to be targeted by nation states intent on replacing your download it's not much of a concern. This is more about creating pressure for everyone to secure everything and to prevent people from seeing what you are doing online.
As annoying as it is I have to give Google credit for making it much more difficult to monitor internet traffic. China can afford to block the latest encryption which hides the severname but encryption by default makes life harder for oppressive regimes.
Transmitting web traffic in the clear means you can be subjected to man-in-the-middle injection attacks. The website you see may or may not be the same as what the website publisher intended.
MITM can be very hard, like you say, or it can be very easy. It's rather easy to setup a WiFi access point and get people to connect through you. In that case you're already in the middle and the MITM attack is easy. Other scenarios are much harder.
“Insecure” in this context mean that any download or upload to the website is not encrypted but sent in clear text.
You shouldn't be able to upload *anything* to it, and who cares if someone else can read what you are downloading -- it isn't secret.
I'm all for privacy & security -- it's why I've used Firefox for more than a decade now -- but at a certain point, the term "paranoia" comes to mind.
"You shouldn’t be able to upload *anything* to it, and who cares if someone else can read what you are downloading — it isn’t secret."
Badly misinformed on both points.
I also meant keystrokes from your keyboard in the direction of the website by "upload". If the site requires logging in, your username and password are also sent in clear text if the site does not have an SSL cert (which makes it "https" instead of "http" without the cert).
And if someone uses the same pw on another website like a bank, then their credentials are known to anyone tapping the transactions.
No, this is not correct at all.
So I haven't tested this fix but this is what I found recommended. Of course this may disable protections so use with caution.
At least it's not as bad as the secret phrase you have to type in to visit sites with broken certs.
---
Put this in your address bar
chrome://flags/
Then go to or copy paste in search
Insecure origins treated as secure
Then enabled...
Then
Treat risky downloads over insecure connections as active mixed content
And disable that.
Bad analogy. The defense of the Alamo was unsuccessful.
Depends on which time-frame you use for reference.
The Alamo is no longer located in Mexico.
By that measure, the defense by the revolutionaries succeeded.
The Alamo is no longer located in Mexico.
Depends on which textbook your children are reading -- some advocate the Reconquista.
No, it doesn't matter what textbook my kid is reading.
The Alamo is absolutely, objectively NOT in Mexico.
He took your quibbling to a new level, and you object?
You find the question of whether the state of Texas is in the United States or in Mexico as "quibbling"? You're not from Texas, are you?
Another idiot who can only win by changing the definitions of common words.
"Battle" is not the same as "war".
Not everything requires quibbling. Some things are just plain wrong.
If you're such an idiot, why did you weigh in?
You want quibbling, so here is some actual quibbling:
As a military effort, the defense of the Alamo against a numerically superior force was a failure.
At the same time, as a PR effort, the defense of the Alamo against a numerically superior force was an unquestioned success.
So helpful are these Big Tech client browsers. Find and use a crippled browser. Consider Mocha Text .dk.
Write your own if you need complete control over your browsing experience.
"Unlike people, you can easily determine whether a web site is insecure."
Factually incorrect. You can readily determine whether a website has some specific deficiencies that would make it less likely to be secure. No, this is not a different way of saying the same thing. Here's a longer way of saying it:
websites may have some red flags that indicate a lack of concern for security, and particularly cautious persons may want to categorically decline to interact with sites that have such red flags. Failing to have such red flags in no way establishes that the site is properly secure. Google is trying to protect Chrome users from lax security by declining to connect to sites that don't implement encryption to transmit web pages. This is not a substitute for knowing and employing best security practices.
Doesn't Chrome have a feature that it will ask you whether you want to allow downloads from the "insecure" site? And a whitelist that you can add your favorite sites to? IIRC that has been my experience.
It did, but perhaps no longer?
According to random peeps on the interwebs, such a feature still exists.
chrome://settings/content/insecureContent
I haven't tried it using it myself, but it seems like it could be effective. Of course, YMMV and all standard disclaimers apply.
That said, I note two things:
(1) I can't even reproduce this supposed problem.
(2) Even if it really is a problem, it seems fairly insignificant.
That's because it only impacts a file download that's linked to by a third party. Nobody should have any issues downloading a file from the hosting site itself, regardless of whether it's secure or not. Of course, as a general matter of best practices, it's better for all sites to be secure, but this specific "problem" really seems like mostly a nonissue.
Happy holidays!
Cheers.
IMO It's got little to do with either security or privacy. Google just wants to make sure nobody else can get their fingers, or ads, into your browsing between the web site and your eyeballs.
That is all the little lock shows-- the path between the server and you is encrypted. Useful if you are sending secret things like your credit card somewhere, but it says nothing about the security of the server or of your endpoint.
With public documents there's little need unless you're really afraid of low-end nation-state MITM attacks as the really good nation-states can forge certificates if they want to.
"That is all the little lock shows– the path between the server and you is encrypted. Useful if you are sending secret things like your credit card somewhere, but it says nothing about the security of the server or of your endpoint."
This is a misinformed opinion. An encrypted connection to a web server assures you that the information has not been altered in transit.
Infomation security has three pillars: Confidentiality, Integrity, and Availability. Encryption can be applied to assure the first two.
I switched over to Firefox a year ago and haven't regretted it.
Note that some of these site have servers listening on both the insecure http (port 80) *and* the secure https (port 443). For example, https://www.ca5.uscourts.gov/ works just fine. The Texas court is very close to secure, the problem is that it contains at least one instance of mixed content. They're close.
Most browsers switched over to defaulting to attempting a secure connection first. Some people use computers where they don't control which browser(s) is/are installed, because their IT administrators have made the selection for them. So the servers still offer unencrypted connections for legacy users. This allows Internet Explorer 4 to still work for people stuck in 1995.
Developments in the digital environment have allowed people to access information and news more quickly. This situation has brought with it some harms along with many benefits. Useful information or news can reach large masses in seconds. A picture or video that harms people's personal rights can also be circulated all over the world with one click. Now everything happens in a short time, which we can call a moment. This situation necessitates the removal or prevention of violations made on the internet at the same speed. For more information https://or.av.tr/erisimin-engellenmesi-ve-icerigin-yayindan-kaldirilmasi/