How a Blue Butterfly Stamp Brought Down One of the Dark Web's Biggest Marijuana Vendors
Operational security remains the Achilles heel for dark web drug vendors.
Go to any U.S. Post Office and you'll see a poster that tells USPS employees how to identify a suspicious and potentially dangerous package. Which means if your package looks like the one below, the odds of it being intercepted and inspected increase dramatically.

Those screening guidelines are meant to intercept packages containing poisons and explosive devices. But as the Justice Department continues to indict suspected drug vendors operating on the AlphaBay and Hansa markets, some new, unpublicized screening tactics are coming to light. The Justice Department built its case against Michael Farber--who allegedly sold nearly $7 million worth of illicit drugs (mostly marijuana) on The Silk Road, Pandora and AlphaBay cryptomarkets under the user names purefiremeds and humboldtfarms—using USPS surveillance.
According to an affidavit filed last month in the Eastern District of California, the postal trail started with a raid on a drug lab in Boston, where agents uncovered several USPS Express Mail shipping labels addressed to Farber. All of these labels used the "waiver of signature" option. According to the affidavit's author, Homeland Security Investigation's Special Agent Matthew Larsen, Express Mail and waiver of signature are both drug-dealing giveaways:

Using data from The Silk Road's server, as well as information provided by an unlicensed bitcoin-for-cash exchanger, Larsen's team was able to tie Farber to a defunct dark web account called purefiremeds, which operated on The Silk Road. Scouring reddit threads—where users frequently post public reviews of vendors—led them to believe the person or persons behind purefiremeds was also running humboldtfarms, a vendor on the AlphaBay site that the DOJ shut down in July. So, federal agents set up a controlled buy on AlphaBay, purchasing "7g Cali Orange Krush Grade A++ Weed," translated as a quarter ounce, from humboldtfarms. The package was intercepted by a postal worker in Fresno, where investigators picked it up. As is often the case with dark web vendors, the package had a fake return address.
This is where it gets really interesting. Nothing about the controlled buy package tied it to Farber. But the parcel did contain some unique qualities: Regular stamps.
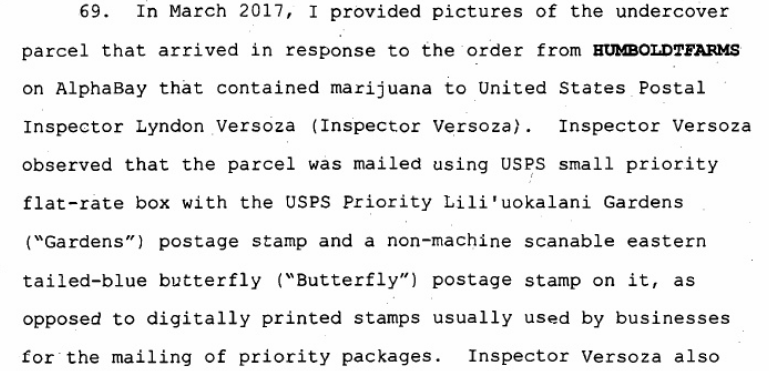
"The more common method" for shipping a large volume of packages, according to the criminal complaint, would be digitally printed stamps containing tracking information. Whoever operated Humboldtfarms preferred to use the kinds of stamps one might put on a birthday card. So, in March 2017, Larsen's team asked Postal Inspector Lyndon Versoza to have USPS staff at Verdugo Viejo Post Office in Gendale, Calif., alert him if they received a large number of packages with the same two stamps. Lo and behold, just such a delivery arrived a week later:

Over the course of several months, the USPS documented the return addresses used for the packages—all of them either fake addresses or fake businesses at real addresses—and documented who dropped them off using surveillance footage. After verifying that each batch of packages contained at least one or two shipments of marijuana, Versoza had police stop the men who dropped them off so that they could be identified (but not arrested).
All told, several people allegedly working with humboldtfarms bought thousands of dollars worth of the Gardens and Butterfly stamps from nearby USPS facilities in California, paying for them in cash:
Eventually, Larsen's team was able to tie together the alleged actors behind humboldtfarms by matching security footage from post office locations with Farber's friends on social media; they also used a GPS tracker on one suspect's car, looked at IRS records, compared public PGP keys, and turned a bitcoin exchanger into a C.I. Five people are now facing charges in the Eastern District of California, which is a hotbed of dark web prosecutions.
As with street level drug prosecutions, the dark web cases coming to light are generally built using the same tactics: One person in the supply chain gets caught due to an operational security issue and turns confidential informant to lessen their punishment.
This leads investigators to a new group of suspects and new operational security flaws. In the humboldtfarms case, it was stamps and the recycling of a PGP key. But I've seen cases where a vendor tried to trademark his dark web handle, another who chose an easily crackable password, and another who tied his dark web account to his personal, public email account.
The reddit angle is also pretty damning, suggesting the trust system used by dark web customers—naming and shaming vendors—actually helps law enforcement identify people who've switched user handles to evade identification.
All of which is to say whatever tech advantages dark web users had in the early days of The Silk Road are now gone. The Justice Department not only has three captured servers with six years of user and transaction data, it knows how the game is played.
Editor's Note: As of February 29, 2024, commenting privileges on reason.com posts are limited to Reason Plus subscribers. Past commenters are grandfathered in for a temporary period. Subscribe here to preserve your ability to comment. Your Reason Plus subscription also gives you an ad-free version of reason.com, along with full access to the digital edition and archives of Reason magazine. We request that comments be civil and on-topic. We do not moderate or assume any responsibility for comments, which are owned by the readers who post them. Comments do not represent the views of reason.com or Reason Foundation. We reserve the right to delete any comment and ban commenters for any reason at any time. Comments may only be edited within 5 minutes of posting. Report abuses.
Please to post comments


Gee, using a quasi-governmental agency to transport your contraband goods may have some security flaws. Who knew?
Shoulda used FedEx.
FedEx doesn't need a warrant to open packages.
I'm making over $7k a month working part time. I kept hearing other people tell me how much money they can make online so I decided to look into it. Well, it was all true and has totally changed my life.
This is what I do... http://www.netcash10.com
Neither does USPS.
USPS needs a warrant or probable cause. 4th Amendment applies to USPS, Google it.
I'm making over $7k a month working part time. I kept hearing other people tell me how much money they can make online so I decided to look into it. Well, it was all true and has totally changed my life.
This is what I do... http://www.startonlinejob.com
FedEx is not anonymous. You have to open an account to ship, and jump through the whole Know Your Customer bullshit.
Damn waste of time and resources.
Yeah, where's the crime? Isn't it legal in California?
All this to prevent people from having a little fun the Nanny State doesn't approve of. When did we get to be such a nation of pantywaists that we'll put up with this shit?
1914?
The Harrison Narcotics Act.
The Harrison Narcotics Act
Justice is served
Hey, if you want to deal in something the government says is illegal, don't use a quasi-government service to ship it.
USPS is probably the best way to ship contraband. You need a warrant to open parcels in custody of the USPS. Likely they would have been caught sooner had they use FedEx or UPS, both of which give law enforcement carte blanche.
An even bigger drug running trick is to get people to buy cheap products on Amazon, especially from China, and then change the mailing address to where you want the drugs delivered.
The label is Amazon looking, so it avoids red flags. It goes to a different address, which is why the tracking will show your package went to Cleveland when you live in Dallas. Amazon gives customer a refund.
I don't understand the sequence. ELI5.
Sounds like using Amazon to launder the address. You sell someone something on Amazon. You never ship them anything. You just use the order to give the package the veneer of legitimacy. Then you use the label to send out the illicit package to the real customer. The patsy complains to Amazon and gets a refund.
"unlicensed bitcoin-for-cash exchanger"
Who is providing the licensing?
It would be interesting to add up what the drug warriors spent per indictment, given that they most likely got the least competent dealers, who were instantly replaced by other dealers.
If "perps" like these can make kazillions of dollars dealing drugs through the USPO, we aren't winning the WoD.
LOL When did you swallow the kool-aid Mike? Of course they know how the game is played. The advantages of crypto currency and the dark web remain. Major dealers shipping out tons of product are the most at risk. They need to take the greatest care, and likely will still leave clues that can lead LEOs back to them. Small dealers that do due diligence and costumers buying only for personal use will be almost impossible to catch.
like Stanley implied I'm startled that people able to profit $5278 in one month on the
computer . Find Out More
?..????????????
Trump"s New Opprunuties See Here
You selling drugs too botman?