Who Keeps Your Data Safe(ish) From the NSA?
For those concerned about National Security Agency interception of commercial data—information that you might share with Facebook, Google, and other online outfits—the Electronic Frontier Foundation keeps a running tally of encryption measures implemented by such firms. Since the NSA often hacks into data links without any legal niceties, such encryption has the potential to dramatically improve security. Even when government officials come with rubber-stamp court authorization in hand, or other tools for compelling compliance, tools like the perfect forward secrecy recently implemented by Twitter can limit the snoops' take. It can even make it impossible for companies to do as the official eavesdroppers ask. That's important for American firms that find their ability to compete both locally and globally seriously hindered by assumptions that their data storage systems are effectively reading rooms for the NSA.
According to the EFF, the table below shows where major online firms stand at the moment in their encryption efforts. This is a moving target, of course, so keep checking back with the EFF for new developments.
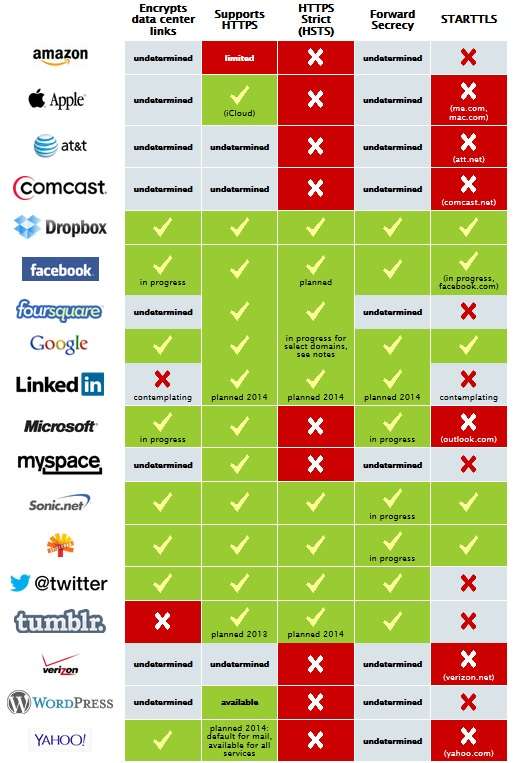
Definition-wise, encrypted data center links are important, because the NSA has been tapping into the free flow of information between servers owned by companies like Google. Encrypting that flow means snoops will nab scrambled and incomprehensible information (unless they crack the encryption).
HTTPS provides a secure connection to Web pages, so that your activity is less easily observed.
HSTS is basically a more secure form of HTTPS.
Perfect Forward Secrecy encrypts each session you spend on a service like Facebook independently, so that even if snoops or hackers get access to one encryption key, they can't retroactively decrypt everything you've done in the past.
STARTTLS is a means on encrypting communications between email servers. Those with their status listed in red, above, provide email to the public, making it a bigger deal than those whose status is in grey, and provide only internal email.
Of course, all of this could be bypassed if the government forces online companies to build in technology that eases wiretapping, which it has already done to telecoms. In that case, look to overseas services—or implement your own encryption.


Show Comments (66)