Journalist Matthew Keys Faces Prison Time Over a Law You've Probably Broken
Keys tells Reason the federal prosecutor railroaded him with felony charges in order to justify his own job.

Matthew Keys, a 29-year-old California-based journalist, tells Reason that he believes he was aggressively prosecuted over a rather innocuous case of internet vandalism because a federal prosecutor needed to justify the continued existence of his own job, and thus used a broad and literal interpretation of a "antiquated and draconian law" to throw the book at Keys.
Keys, who was sentenced to two years in prison last week, was indicted in 2013 under the Computer Fraud and Abuse Act (CFAA) for the alleged crime of sharing a password with hackers affiliated with Anonymous — the decentralized network of activist techo-criminals known for creating digital mischief at the expense of governments, corporations and other powerful institutions — who briefly defaced a single page on the Los Angeles Times' website in 2010.
Considering Keys faced a maximum of 25 years in prison and $750,000 in fines for his three felony convictions of conspiracy to transmit information to damage a protected computer, transmitting information to damage a protected computer, and attempted transmission of information to damage a protected computer, one could argue his sentence was light. But when you examine the minimal damage done by his alleged crime, any hard time at all seems excessive.
The "damage" done in this case occurred when a hacker changed a headline from "Pressure Builds in House to Pass
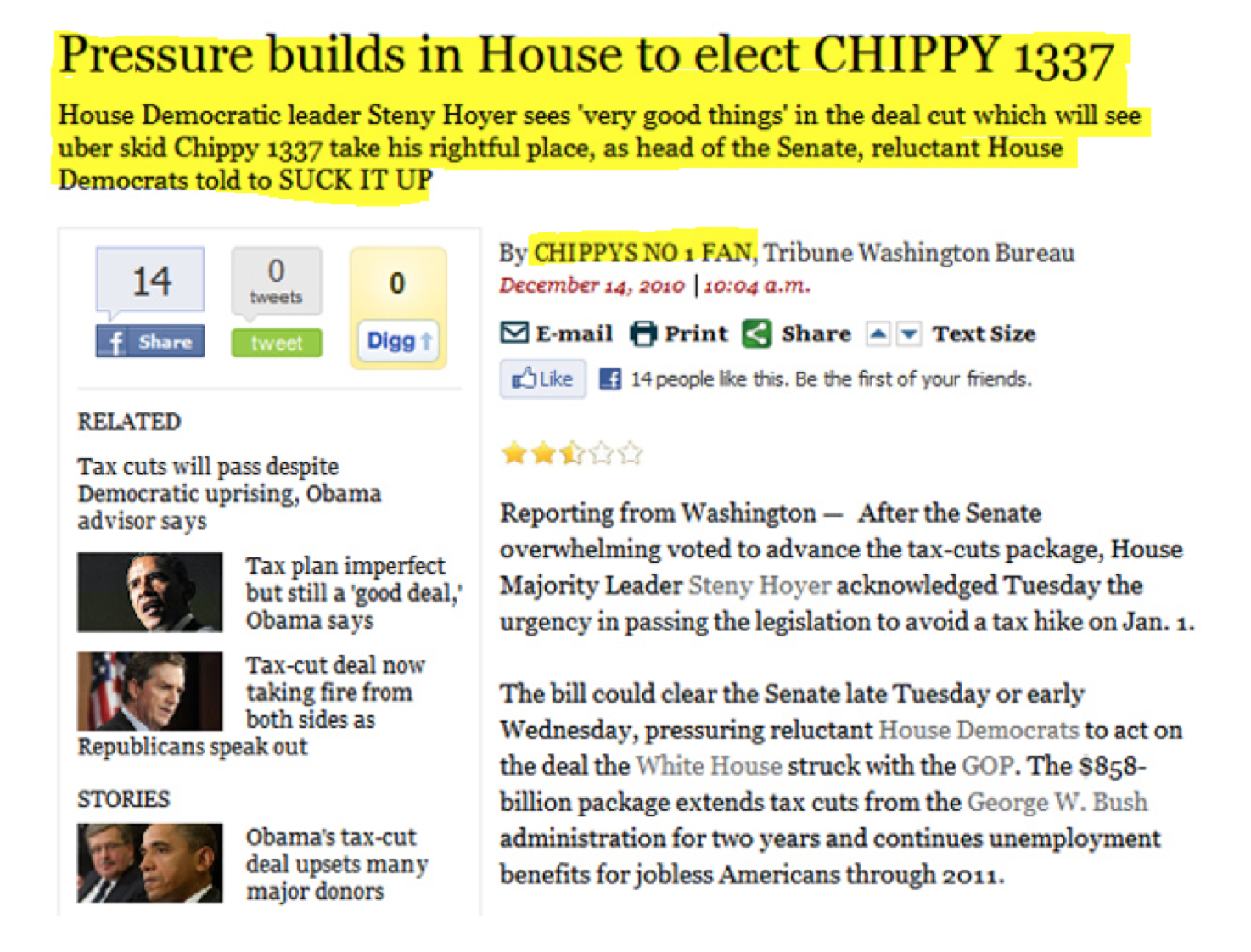
Tax-Cut Package" to "Pressure Builds in House to Elect CHIPPY 1337." The altered headline was discovered within 40 minutes, and corrected within three minutes. That's it.
Prosecutors alleged that Keys was a disgruntled ex-employee of Sacramento's KTXL-TV (which along with the Times is owned by the Tribune Company) and that he shared his log-in credentials for Tribune websites with the hackers, instructing them to "go fuck some shit up."
But Keys tells Reason that he believes the government's true motivation was to bully him into revealing the source material he had gathered in the months he spent investigating Anonymous by infiltrating some of their chat rooms.
Though Anonymous has been known to hack ISIS and the government of Iran, the hacktivist group has long been a thorn in the side of the U.S. government. In numerous incidents over the past decade, the hackers have stolen and leaked the personal data of thousands of government employees, often as a direct protest to policies members of the group find objectionable, like the Trans-Pacific Partnership (TPP) trade agreement.
Keys says that in 2012, FBI agents investigating Anonymous asked him to hand

over the investigative materials he had amassed, in order to help with the feds own inquiry into the secretive hacker enclave. Keys refused this request. Then at 5:45am on October 4, 2012, he was awoken by the sound of FBI agents executing a search warrant on his apartment. The agents grilled Keys about his involvement with Anonymous for about two hours before they left, taking his computer with them.
Without hearing another word about it from the government, on March 14, 2013, Keys found out via Twitter that he had been indicted on three felony counts, all related to the brief defacement of the Times' web page. On October 7, 2015 a jury that deliberated for less than a day sealed his fate, and the young journalist became a convicted felon facing the prospect of spending much of his adult life in federal prison.
Keys, who is appealing his conviction, steadfastly maintains his innocence. He says the government's claim of his motive makes no sense because he left the company on his own accord and maintained cordial relationships with his former colleagues and supervisors, even pitching them a few potential stories.
He explains, "My motivation for leaving was that there were no new opportunities there for me to pursue. The company had instituted hiring freezes, promotional freezes, salary freezes. They were laying people off left and right. I stayed there for two years and I felt like I had grown enough." But, he says, after doing his time in the mid-sized Sacramento market, he was ready to move to the East Coast and try to make it in the big leagues.
Eight months after leaving the Tribune-owned station, Keys got the opportunity to move to New York and work for Reuters as their deputy social media editor. Keys says, "My career focus was not on Tribune. It was my first professional opportunity in news. I did work there that I'm very proud of. I would not have wanted to undermine everything I did there by encouraging hackers to deface Tribune's digital property."
The reason Keys believes he has been prosecuted so vigorously is because, "It's Sacramento. How many computer crimes cases come across this prosecutor's desk? Not a whole lot." He adds that the prosecutor needs to justify his existence and that Keys' was a "case of opportunity for [the prosecutor] after he had lost a case involving this same group of hackers."
Keys continues, "Violations of the CFAA qualify as crimes of terrorism," and more prosecutions which feature the t-word mean more federal dollars for the jurisdiction in question.
But, he adds, the CFAA covers "everything from stealing trade secrets to sharing your Netflix username and password." He also noted that Reddit's co-founder Aaron Swartz committed suicide after being aggressively prosecuted under the CFAA for the crime of mass downloading academic journals from a Massachusetts Institute of Technology (MIT) server.
Keys describes the CFAA as a "antiquated" 30-year-old law written before the world wide web even existed, and argues that it includes such broad language that ordinary Americans are almost always in violation of some portion of it. He admits being particularly concerned with the law's ramifications on his own profession, journalism.
"Let's say you share your Netflix password with a friend or a family member," Keys explains. "You also happen to be working on a story about a massive leak of government secrets. And the government would really like to know what you have. They could do exactly what they did to me, to you. They'll investigate this crime to get to your source material. That seems like it shouldn't be allowed to happen."
To anyone who might think he's overstating the case, Keys adds, "Consider that [the Obama administration's] Justice Department has impersonated Associated Press reporters and gotten the phone logs of AP reporters. They've tried to go after two journalists, [the New York Times'] James Risen and [Fox News'] James Rosen, in two different leak investigations, threatening them both with jail time if they didn't reveal their sources."
Keys concedes that many people might not want to believe that an administration which has described itself as "the most transparent in history" would go after someone for so benign a crime. But in 2015, President Obama actually proposed broadening the law even further, as well as increasing penalties for violations.
Following his sentencing, Keys wrote on Twitter that he and his lawyers are "not only going to work to reverse the conviction but try to change this absurd computer law, as best we can." He also says he hopes if any good can come out of his own prosecution, it would be for the public to understand how easily the perfect storm of an ambitious prosecutor and aggressive investigators using an arbitrarily applied law can gather to put the squeeze on someone who is an inconvenient obstacle to them.
"When you really think about it that way," Keys says, "it doesn't seem so conspiratorial, does it?"
UPDATE: An earlier version of this article mentioned the maximum fine Keys faced as $500,000, it has been corrected to $750,000.
